The internet of things might not be a new term you might have came across. Right? We can see IoT devices crowning some major benchmarks all across the business world. People are totally convinced with the fact that IoT would be replacing human labor anytime soon. But everything comes with vulnerability or a price. But Portnox is on other verge with IoT devices by presenting IoT fingerprinting.
IoT devices provide a growing number of security concerns that affect all organizations since they are more prone to vulnerabilities and are therefore excellent targets for assaults. To keep hackers from using these devices as a doorway into the corporate network, businesses of all sizes must adequately secure them. But as IoT device numbers increase and networks get more complicated and spread, it gets harder and harder to detect and manage access to these devices across a given network, let alone secure them.
But, here comes Portnox at a rescue to tackle network security issues related to IoT devices.
Network security company Portnox announced on Wednesday that it is enhancing its Cloud NAC-as-a-Service with IoT fingerprinting features to make it easier for businesses to identify and approve devices on their networks.
Portnox: Overview
Zero trust access control firm Portnox specializes in network security. Israel and the United States both host Portnox offices. Agile, resource-constrained IT organizations can proactively solve today’s most important security concerns thanks to Portnox’s cloud-native zero trust access control and cybersecurity basics. In order to boost their organizational security posture, hundreds of businesses have used Portnox’s multi-award-winning security technologies to impose strict network access, endpoint risk monitoring, and remediation rules. Portnox makes it possible for businesses, regardless of size, geographic distribution, or networking architecture, to deploy, scale, enforce, and maintain these crucial zero trust security policies with an unprecedented level of simplicity by doing away with the need for any on-premises footprint typical of traditional information security systems.
IoT Fingerprinting by Portnox
Portnox is a company with offices in Austin, Texas, and Israel. It asserts to be the first to offer a cloud-native solution for assisting mid-market and enterprise companies in addressing IoT security concerns. This is done as part of a zero trust approach to security. In terms of more general security, the zero trust element of SASE architectures means that no user or device is considered to be reliable and that any device utilizing network resources must first provide identification documentation in order to access the network on a least-privilege basis as determined by contextual policies.
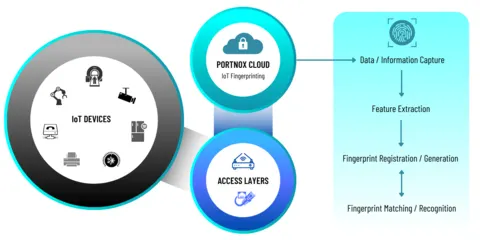
The new IoT fingerprinting and profiling features from Portnox, which are now accessible via the Portnox Cloud, enable enterprises to quickly and precisely identify, verify, authorize, and segment IoT devices across their network to achieve an effective zero trust security posture.
This IoT fingerprinting techniques are made to profile IoT devices that are connected to a network but are unable to fully identify themselves by communicating details like their model, version number, or even their type owing to a lack of storage or processing capability.
“The next logical step in implementing our vision of streamlining access control and endpoint security for mid-market IT teams was to incorporate an IoT fingerprinting solution into our cloud-native platform. Customers now have complete visibility of all IoT devices being used on their individual networks thanks to Portnox.”- said Denny LeCompte, CEO at Portnox.
What does IoT fingerprinting offer to Network Security?
With the most recent solution addition, the Portnox Cloud now gives businesses:
- Complete network-wide device visibility and access policy enforcement for all significant device groups, including IoT, BYOD, and managed devices
- With the use of artificial intelligence and machine learning, IoT fingerprinting and profiling accuracy has increased.
- strengthened corporate zero trust security postures that take into consideration all on-site and remote devices and access layers
Prevents Address Spoofing Risks
Additionally, organizations will be able to access new features including automatic policy mapping based on fingerprints and the use of fingerprinting data to mitigate MAC Address spoofing concerns. There’s no need to worry if that MAC address is a printer on the third floor or a hacker attempting to get past the firewall. See the type of device, the maker, the OS, the version, and more quickly! With more being added daily, we currently recognize over 260,000 distinct IoT device models from 27,000 different brands and 30,000 operating systems. Portnox NAC-as-a-Service profiles IoT devices with 95% accuracy by combining numerous passive fingerprinting techniques.
Control of Access
The NAC service verifies a user’s identification and the types of access they are permitted on a network when they attempt to access it using a wired or wireless device. Additionally, it will examine the security status of the device being used, ensuring that an antivirus is installed, vulnerabilities are fixed, and the appropriate ports are open or closed. If the required security posture is not followed, the NAC-as-a-Service does not allow the device to access the network.
Portnox IoT Fingerprinting Cost
Only the enterprise version of Portnox’s NAC-as-a-Service will have the IoT fingerprinting feature. The new feature won’t cost you anything more. The fingerprint data will instantly start appearing if an organization is already utilizing NAC-as-a-Service. NAC-as-Service costs $4 per device per month at the entry level.
Future of IoT Fingerprinting
The new Portnox solution offers precise IoT fingerprinting and profiling through the use of artificial intelligence and machine learning. Portnox is exploring new approaches to enable agentless risk assessment policy enforcement and data gathering alternatives. This is done solely to tackle problems such as to improve IoT fingerprinting access and automate micro-segmentation and quarantining for IoT devices.
In fact, according to Juniper Research, there will be 83 billion IoT connections globally by 2024. In addition, the Ponemon Institute discovered that 94% of businesses think a security incident brought on by unprotected IoT devices or applications could end badly.